Enable Generation of dCVV2 Codes to Fight Fraud
Last Updated on November 30, 2020 by
One way some ecommerce merchants have avoided the EMV liability shift* is through the use of CVV2 codes on all Card Not Present (CNP) purchases. After all, the CVV2 code is there for security purposes as a way to thwart cybercriminals who steal credit card numbers and hope to use them on sites that don’t require the additional security code.
* The EMV liability shift places financial liability for fraud on the merchants instead of the card networks covering it themselves. It applies to any merchant that doesn’t use EMV-compliant credit card readers or use CVV2 codes on their ecommerce sites.
However, some merchants are storing static CVV2 numbers on their sites, which puts them at risk of being hacked and stolen. If crooks can get the CVV2 numbers, then that gives them access to CVV2-protected sites and creates the potential of even more theft and loss. Right now, credit card numbers are no good on CVV2-protected sites without that simple 3-digit code, which means getting access to stored codes can mean all kinds of fraud problems.
So Visa has developed the means of generating a dynamic CVVs (dCVV2) code as a way to eliminate the problem of storing the static CVV2 codes.
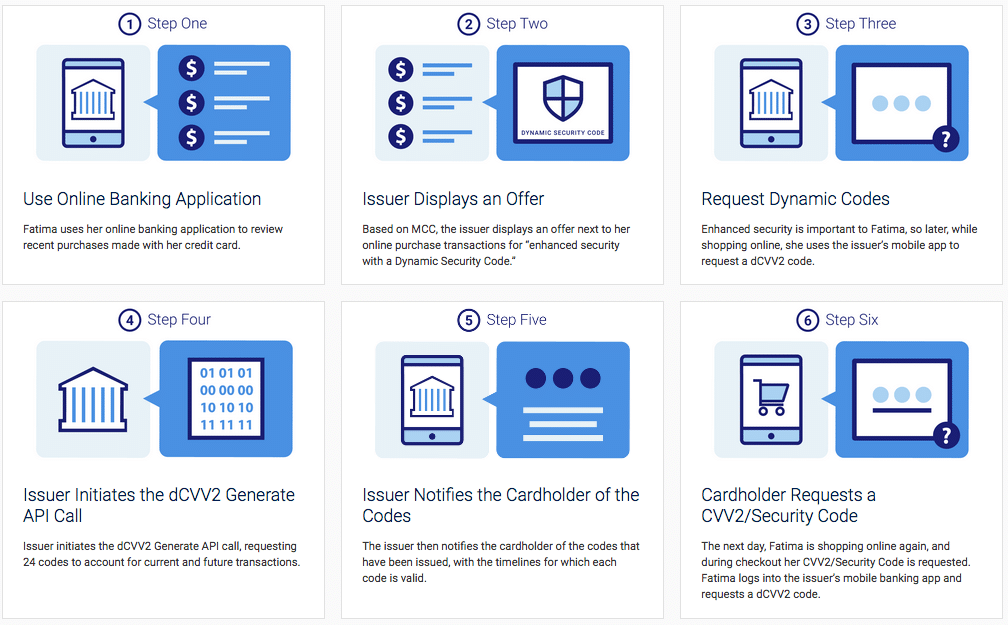
Here’s Visa’s explanation of how the dCVV2 codes work:
Fatima is an avid online shopper and, based on KYC data, the issuer displays an offer for Fatima to help increase security with the use of dynamic security codes during her online shopping.
Later, while shopping for her cousin’s wedding, Fatima remembers the offer and accesses her issuer’s banking application and requests the “Dynamic Security Code” for her credit card. The code is delivered to Fatima, and at checkout she uses the dCVV2 value she has been issued.
The next day, she is shopping online for her nephew’s graduation, and she again uses the issuer’s mobile app to request a dCVV2. The issuer had requested multiple codes from Visa with Fatima’s original request the previous day, so simply forwards her the current valid value – without making another call to the Visa API. Fatima uses this new value while checking out to complete a successful Card Not Present transaction.
Of course, this will greatly help reduce fraud on two fronts: For one thing, it eliminates the possible theft of stored CVV2 numbers. Even if those numbers were kept in a separate database on a separate server, that’s still a risk. That protects ecommerce sites that currently require CVV codes.
But this can also help reduce fraud by encouraging cardholders to be more mindful of how and where they use their credit cards, and to take an extra step to prevent theft of their information.
In some ways, this new practice even follows the EU’s
Visa says this can also reduce, if not eliminate, the need to reissue cards that were compromised in data breaches. Of course, this would require widespread acceptance of dCVV2 by not only the cardholder but the merchant as well.
And that’s where we see this getting a little sticky.
While we appreciate the effort at security and fraud reduction, it seems like this might be a little frustrating for users. It’s no longer just a matter of pulling out a credit card to get the numbers off the front and back. Now we have to pull out our cell phone, open the app, request a new dCVV2, and wait for it to appear.
Of course, when it’s written out like that, it sounds like a really lazy first world problem. But we can see how it might be a sticking point for some users.
Still, anything that people can do to improve their own security would be very helpful. And even if only a third of all credit card holders would participate in the dCVV2, it would eliminate an awful lot of fraud, so we don’t expect this to go away.
There may even be a time, in a few years, where the dCVV2 is a requirement and not an option. The process will probably also be a lot smoother and easier, and we should see a serious decrease in overall credit card fraud.
If you’d like to learn more about how to use Visa’s dCVV2 functions in your own business, Corepay can help. To learn more, please visit our website or call us at (866) 987-1969.
Photo by Visa
We appreciate you following Corepay’s blog. Let’s collaborate, send us your article suggestions, questions, and/or feedback to: [email protected].